You can provide web-based device management by installing the Security Device Manager (SDM) on Cisco Routers. With SDM, you can make simple and advanced settings on your Router.
How to Enable NAT on a Router Using SDM
NAT converts private IP addresses into global IP addresses and, as a result, brings the computer on the local network to the Internet.
Private IP addresses are defined in RFC1918.
Computers or devices with specific IP addresses on the LAN access the Internet through NAT.
In this article, we will use SDM for Basic NAT configuration. If you haven’t installed SDM before, you can check out this article.
How to Configure NAT with Security Device Manager
We will use GNS3 and VMware Workstation to configure NAT with SDM. Therefore, a virtual machine in VMware must be prepared, and the network adapter must be configured as Host-Only.
Step 1
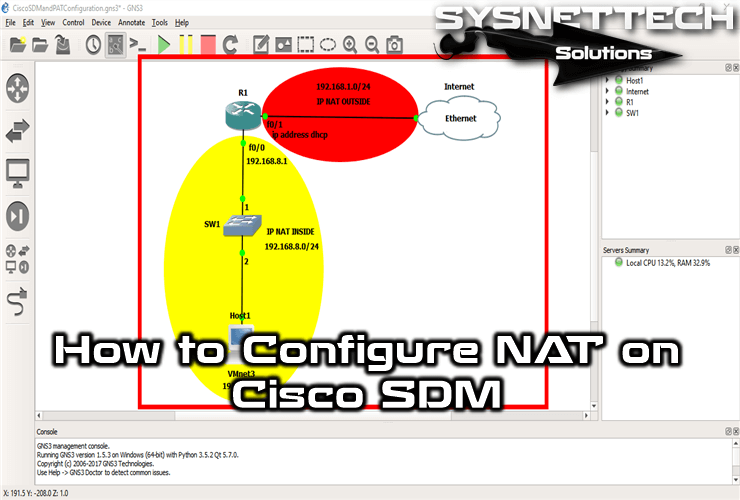
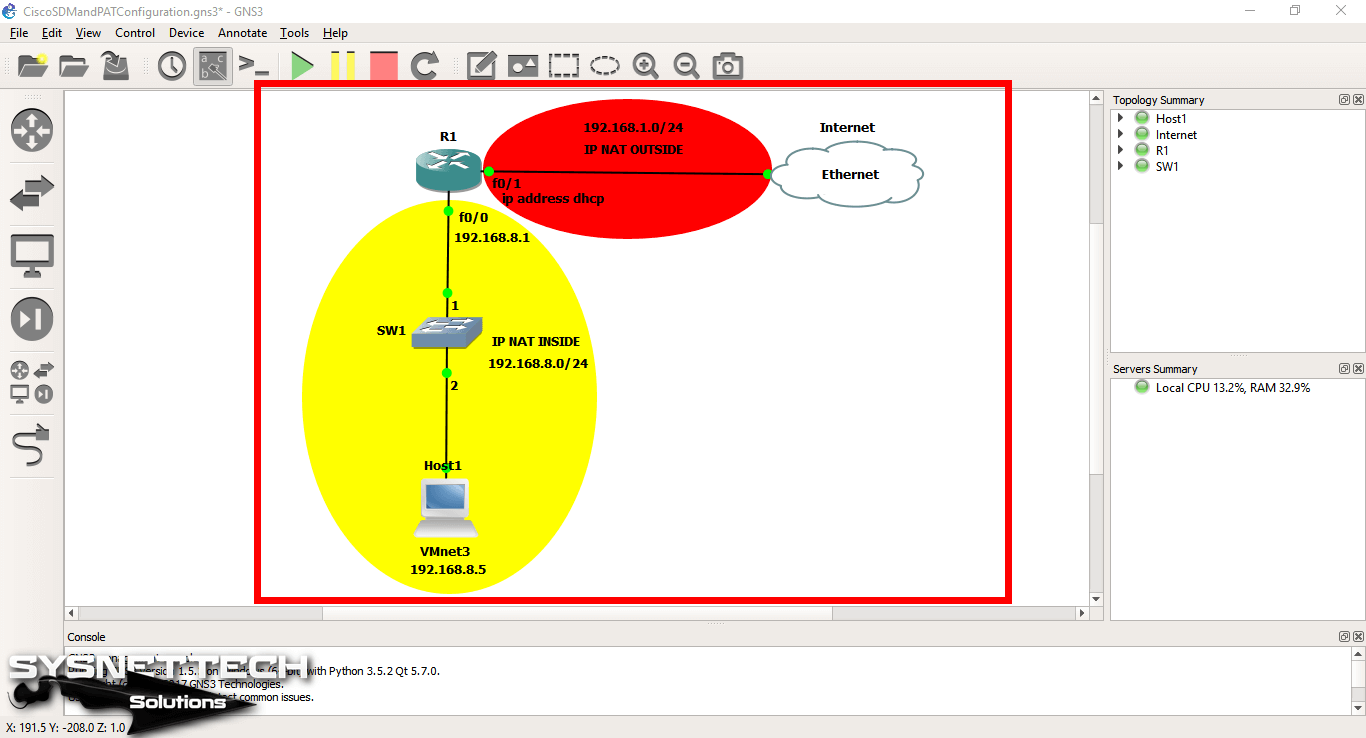
After running GNS3, create a simple network topology, as shown in the image below.
Step 2
Open the SDM via the virtual machine and connect the Router. You can also access the Router via a browser.
After accessing the SDM, click Configure.

Step 3
Click on the Configure tab and click on the NAT on the left.

Step 4
Select the simple NAT option and then click the Launch the selected task button.

Step 5
Click the Next button in the NAT Wizard window.

Step 6
In this step, you need to select the interface that is connected to the Internet because you must configure Outside and Inside in NAT operation.

Step 7
Now select the interface connected to the Internet according to the network topology.

Step 8
After selecting the FastEthernet0/1 interface, you need to choose the IP address range.

Step 9
After making the necessary settings for NAT, click Next to continue.
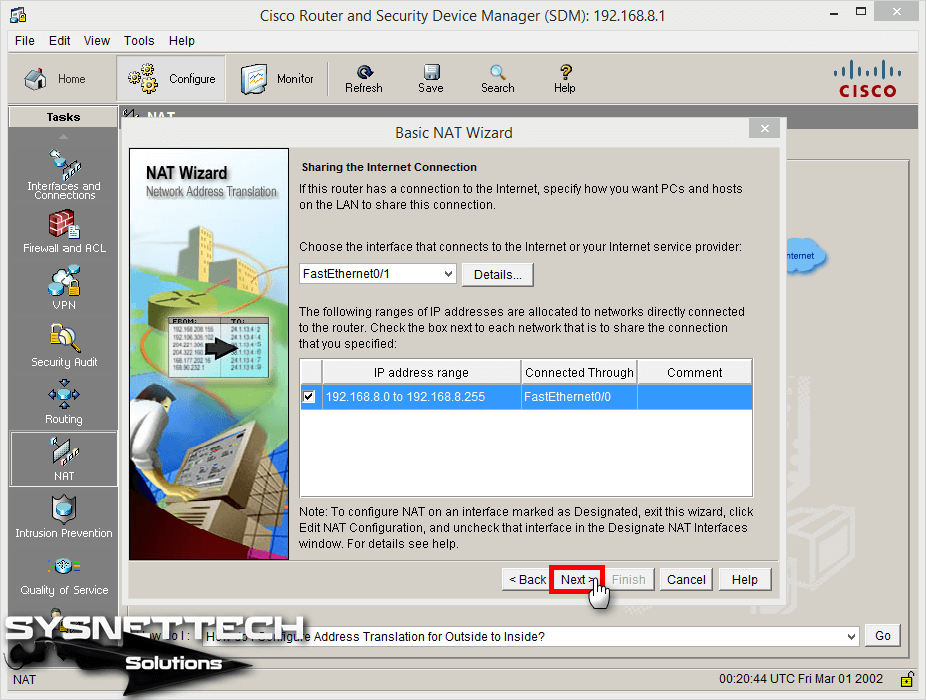
Step 10
Click the Finish button to apply the Basic NAT commands.
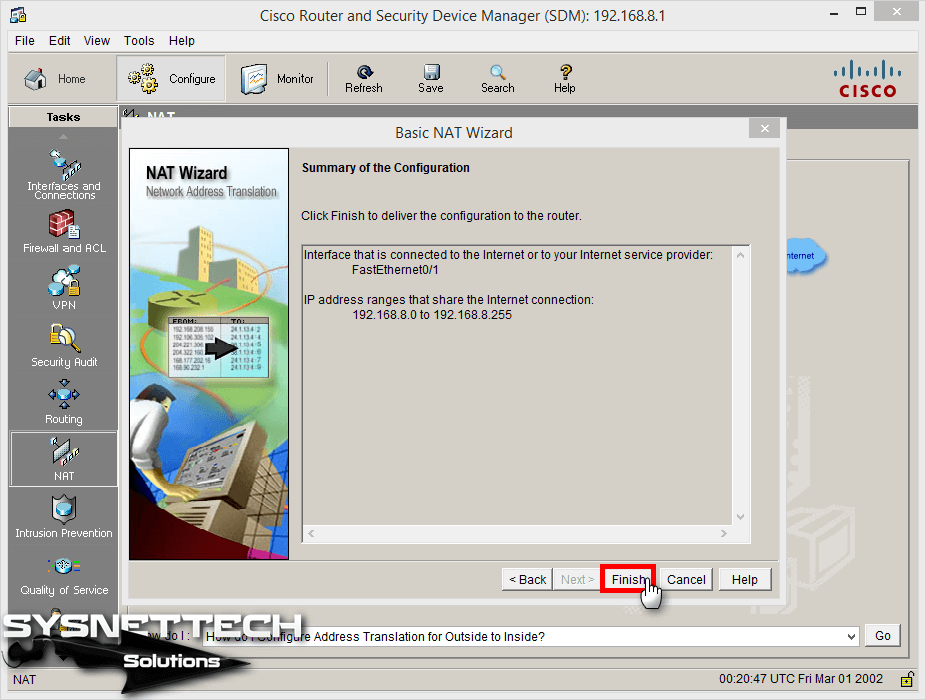
Step 11
SDM has successfully sent commands to the Router!
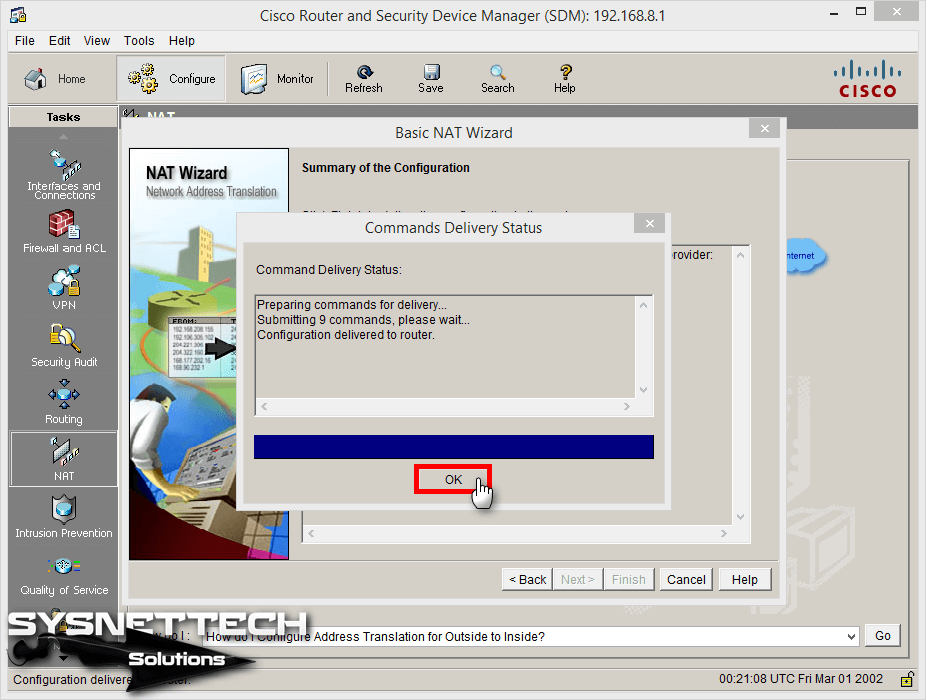
Step 12
You can review the summary of the NAT configuration.

Step 13
Check that the ping from the virtual machine installed on VMware to Google DNS servers has successfully performed as follows.

Step 14
To display the NAT address translations, execute the show ip nat translations command at the command prompt.
When you examine the NAT translations in the Router’s CLI console, you can see that the 192.168.8.5 IP address is translated to the 192.168.1.101 IP address.

Step 15
Examine the NAT outputs on the Cisco Router when you access Google from the virtual computer.

Step 16
On the Router, execute the show ip nat translations command and check the output.
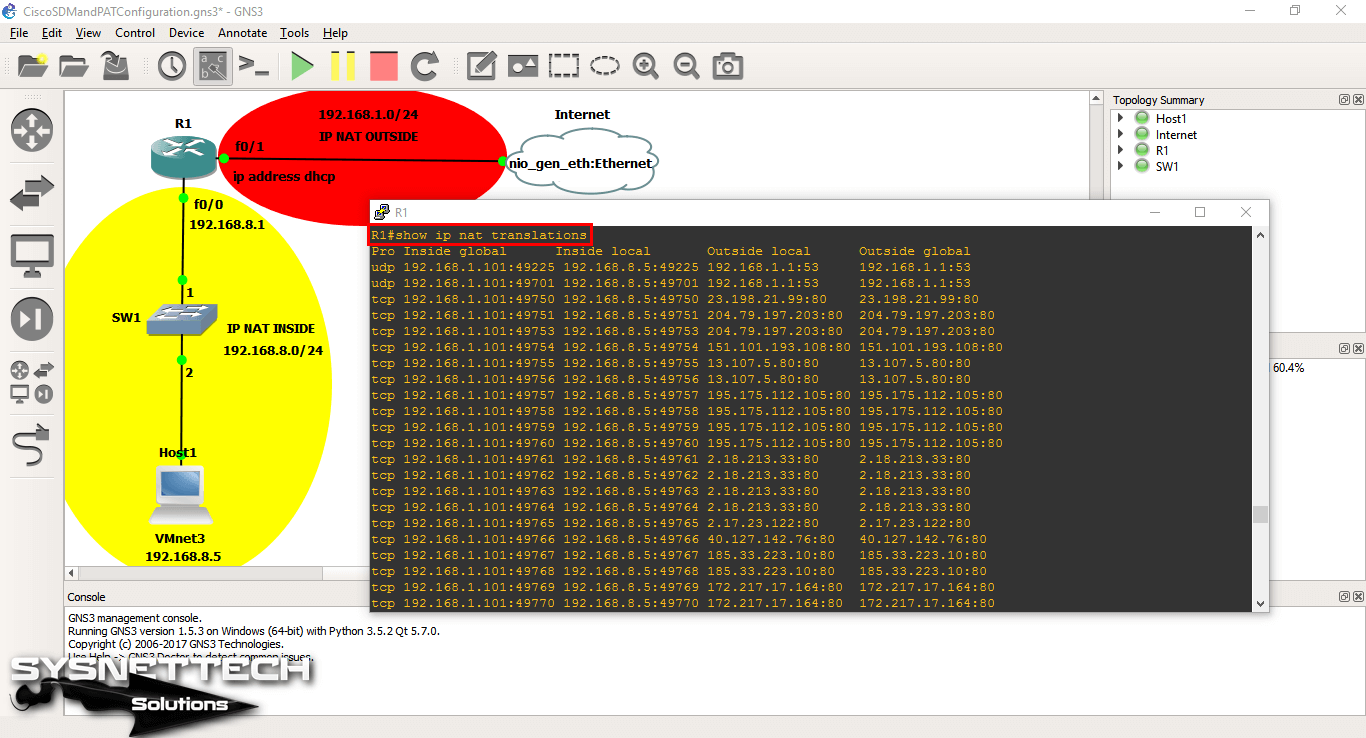
Step 17
Finally, execute the show ip nat statistics command and examine the converted transaction number.

Show Commands
R1#show running-config
Building configuration...
Current configuration : 1449 bytes
!
version 12.4
service timestamps debug datetime msec
service timestamps log datetime msec
no service password-encryption
!
hostname R1
!
boot-start-marker
boot-end-marker
!
no aaa new-model
memory-size iomem 5
no ip icmp rate-limit unreachable
ip cef
!
no ip domain lookup
ip auth-proxy max-nodata-conns 3
ip admission max-nodata-conns 3
!
crypto pki trustpoint TP-self-signed-4279256517
enrollment selfsigned
subject-name cn=IOS-Self-Signed-Certificate-4279256517
revocation-check none
rsakeypair TP-self-signed-4279256517
!
username ciscosdm privilege 15 secret 5 $1$P8AQ$58kw7DHT7YUj3far7KDoM.
!
ip tcp synwait-time 5
!
interface FastEthernet0/0
ip address 192.168.8.1 255.255.255.0
ip nat inside
ip virtual-reassembly
duplex auto
speed auto
!
interface FastEthernet0/1
ip address dhcp
ip nat outside
ip virtual-reassembly
duplex auto
speed auto
!
ip forward-protocol nd
!
ip http server
ip http authentication local
ip http secure-server
ip nat inside source list 1 interface FastEthernet0/1 overload
!
access-list 1 remark SDM_ACL Category=2
access-list 1 permit 192.168.8.0 0.0.0.255
no cdp log mismatch duplex
!
control-plane
!
gatekeeper
shutdown
!
line con 0
exec-timeout 0 0
privilege level 15
logging synchronous
line aux 0
exec-timeout 0 0
privilege level 15
logging synchronous
line vty 0 4
login local
transport input telnet
!
end
R1#
R1#show ip nat statistics
Total active translations: 85 (0 static, 85 dynamic; 85 extended)
Outside interfaces:
FastEthernet0/1
Inside interfaces:
FastEthernet0/0
Hits: 2977 Misses: 94
CEF Translated packets: 2921, CEF Punted packets: 297
Expired translations: 62
Dynamic mappings:
-- Inside Source
[Id: 1] access-list 1 interface FastEthernet0/1 refcount 85
Appl doors: 0
Normal doors: 0
Queued Packets: 0
R1#
R1#show ip nat translations
Pro Inside global Inside local Outside local Outside global
udp 192.168.1.101:49225 192.168.8.5:49225 192.168.1.1:53 192.168.1.1:53
udp 192.168.1.101:49701 192.168.8.5:49701 192.168.1.1:53 192.168.1.1:53
tcp 192.168.1.101:49750 192.168.8.5:49750 23.198.21.99:80 23.198.21.99:80
tcp 192.168.1.101:49751 192.168.8.5:49751 204.79.197.203:80 204.79.197.203:80
tcp 192.168.1.101:49753 192.168.8.5:49753 204.79.197.203:80 204.79.197.203:80
tcp 192.168.1.101:49754 192.168.8.5:49754 151.101.193.108:80 151.101.193.108:80
tcp 192.168.1.101:49755 192.168.8.5:49755 13.107.5.80:80 13.107.5.80:80
tcp 192.168.1.101:49756 192.168.8.5:49756 13.107.5.80:80 13.107.5.80:80
tcp 192.168.1.101:49757 192.168.8.5:49757 195.175.112.105:80 195.175.112.105:80
tcp 192.168.1.101:49758 192.168.8.5:49758 195.175.112.105:80 195.175.112.105:80
tcp 192.168.1.101:49759 192.168.8.5:49759 195.175.112.105:80 195.175.112.105:80
tcp 192.168.1.101:49760 192.168.8.5:49760 195.175.112.105:80 195.175.112.105:80
tcp 192.168.1.101:49761 192.168.8.5:49761 2.18.213.33:80 2.18.213.33:80
tcp 192.168.1.101:49762 192.168.8.5:49762 2.18.213.33:80 2.18.213.33:80
tcp 192.168.1.101:49763 192.168.8.5:49763 2.18.213.33:80 2.18.213.33:80
tcp 192.168.1.101:49764 192.168.8.5:49764 2.18.213.33:80 2.18.213.33:80
tcp 192.168.1.101:49765 192.168.8.5:49765 2.17.23.122:80 2.17.23.122:80
How to Enable NAT with SDM ⇒ Video
You can watch the video below to enable NAT and also subscribe to our YouTube channel to support us!
Conclusion
In this article, we examined how to enable Network Address Translation with SDM on a Router on a network. You can also do this by using the CLI command prompt. Thanks for following us!