The OSI model is a framework for standardizing telecommunications and computing systems. The International Organization for Standardization (ISO) first proposed the OSI technology in the late 1970s.
This standard provides a structured approach to the design and implementation of network systems. In addition, in this article, I will explain what the OSI model is, its layers, and how it works.
What is the OSI Model (Open Systems Interconnection)?
The OSI model is a reference framework for communication systems. It is a functional guideline for communication tasks. Therefore, it does not specify a communication standard for such tasks. However, many standards and protocols follow the OSI standard guidelines.
History
In the 1960s and 70s, they created many network technologies. Each of them is based on a specific hardware design. However, they made these systems as a single piece. We can call this a monolithic architecture. Therefore, designers had to deal with all the elements.
These elements are parts of the transmission chain. This chain includes physical connection devices, software and hardware protocols, and application programs.
It is not practical to see the chain as a monolithic whole. Even the slightest change necessitates altering all the elements. The original Internet design of the US Department of Defense is a four-layer plan. This plan dates back to the 70s but is still in use. In other words, the first level is the Network Access Layer.
In each case, it sends information about the hardware system used. Different protocols depend on the type of physical network. The Network Layer also means the Internet Layer. In short, it allows data to be sent over different physical networks.
This section within the OSI transmits info to the target machine. Transport protocols such as IP are related to the Transport Layer. It also controls the establishment and termination of the connection. Data flow control manages the retransmission of lost info and the transmission between two systems. The most critical protocols here are TCP and UDP.
The last level is the Application Layer. This application layer directly serves user programs. For instance, programs like web browsers, email clients, FTP clients, and TELNET run in this environment.
In 1978, ISO proposed a communication model for networks. We can express this standard as the OSI model. On the other hand, its acronym is Open Systems Interconnection.
The OSI model divides the transmission chain into various modules. Modules interface with adjacent ones. This design has two advantages: Changing a module does not affect the entire chain. It also provides interoperability between different manufacturers. This means that two different communication software can use the same physical tools.
What are the Main Components of the OSI Model?
The OSI model has two main components. The first component is a network standard called the Basic Reference Model or Server Layer. On the other hand, the second component is a set of specific protocols.
The Internet model inspires the network layout. However, it has no more similarities than that. It is based on a seven-layer model. The primitive Internet was based on four layers. Currently, all developments are based on the seven-level standard.
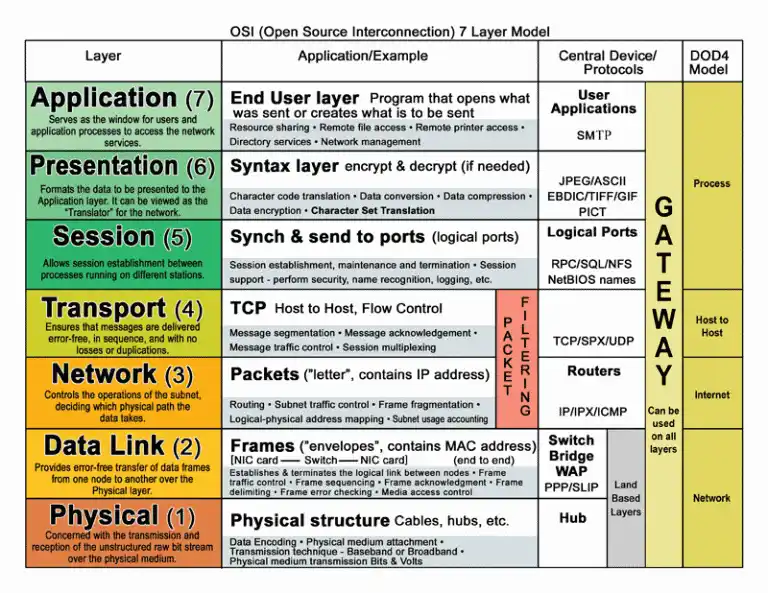
These levels are Physical, Connection, Network, Transport, Session, Presentation, and Application. Each level performs a specific function. In addition, each level is separated from adjacent ones by known interfaces.
This model is a conceptual abstraction. However, this abstraction has been adapted to physical reality. The results of its application are beneficial. The basic concept is like putting the address and information in a letter.
A letter follows a series of operations in the postal service. These operations deliver the letter to the recipient. The recipient receives the letter from the mailbox and reads it. Similarly, devices used in networks operate at specific levels.
For example, a Hub device only works at level 1. This device amplifies and transmits the signal through all ports. A Switch operates on layers 1 and 2. A Router operates on layers 1, 2, and 3.
Finally, a user workstation usually handles layers 5, 6, and 7. The software allows each level to communicate with adjacent layers. Also, each layer uses a specific protocol. It adds some additional information to the packet header. This information is called the Protocol Header.
What are OSI Layers?
The schematic description of the various layers that make up this model is as follows:
1) Physical Layer
The physical layer is trustworthy for sending bits of information over the line used for transmission. It also deals with the physical and electrical properties of the various components. It also determines the speed and direction of transmission. Plus, transmission can be unidirectional, bidirectional, or full-duplex.
In addition, the interpretation of electrical signals is also the responsibility of this level. The mechanical aspects of the connections and terminals are also the responsibility of this level. It is responsible for converting a binary information packet into a pulse suitable for the physical medium used in the transmission.
These pulses can be electrical (cable transmission), electromagnetic (wireless transmission), or light (optical transmission). When operating in receive mode, it converts these pulses into binary data packets. These data packets are transmitted to the link level.
For example, this level defines the dimensions of the coaxial Ethernet cable. The BNC connectors used are also among the components at this level. Another example of standards related to this layer are RS-232 and X.21 for serial communication.
2) Link Layer
The link layer transfers messages from the physical level to the network layer. It also specifies how info will be transmitted in a given medium. In short, it defines the frames of Ethernet packets. It also specifies addresses and checksums.
In addition to local addressing, error detection and control are among the functions of this level. It also deals with info integrity and transmission reliability. Therefore, it groups information into blocks.
Each block contains a checksum that allows the receiver to check its integrity. The receiver verifies the received datagrams. It also sends a control message for corrupted datagrams. The PPP protocol is an example of this layer.
We can divide the link layer into two sub-layers:
- Logical Link Control (LLC): It defines the way data is transferred by providing services to the upper levels.
- Medium Access Control (MAC): This sublayer acts as a controller for the network adapter. The network card driver is sometimes referred to as the “MAC driver.” However, we usually know the physical address as the MAC address.
The main task of this layer is to control the use of physical media. It also allows several sets to use the transport medium simultaneously. The CSMA/CD mechanisms used in Ethernet are an example of this sublayer.
The IEEE 802.11 standard defines the rules for operating in WLAN. It also defines two sub-levels of the OSI architecture. The protocols of the 802.x branch cover the technology of local and metropolitan area networks.
802.11i has been approved to address security in wireless networks. It is based on the TKIP encryption algorithm. It also supports the more secure AES.
3) Network Layer
The network layer deals with the transmission and routing of datagrams. It can be complex in large networks like the Internet. It does not deal with packet errors or losses. For example, it defines the Internet address and route structure.
The network level section uses two types of packets: data and route update packets. As a result, we can divide them into two:
- Transport: It works to encapsulate data. In this case, it uses data packets with the IP protocol.
- Switching: It shares network connection information. That is why its activity is user-generated.
That is why routers work in this section and use route update packets. It also includes the ICMP protocol. ICMP generates messages when transmission errors occur. It has an echo mode that can be verified using PING.
Standard protocols in this layer are X.25 and IP.
4) Transport Layer
The transport layer confirms the reliability of the service. It also defines the quality and nature of the data presentation. After that, it determines when and how retransmission is used. It breaks the message into pieces, sorts them, and forwards them to the network level.
During reception, it reorders the datagrams. It also multiplexes a transport link between data links. This allows the data to share the same stream.
UDP is the protocol we are using here. For this reason, some application programs on the Internet use it.
5) Session Layer
It is an extension of the transport layer. It provides dialog control and synchronization. However, many applications do not use it.
For example, Internet communication does not use it. Some authors state that the session segment has no practical use.
6) Presentation Layer
The presentation layer deals with the semantic aspects of data. It also defines the syntax of the data. It provides communication between machines that use different internal representations. For example, it describes the transfer of floating-point numbers.
It is also suitable for crypto applications. In theory, it presents the info to the application segment. It converts the received data into formats. In short, it includes text, image, and audio formats.
The client and server must negotiate the format to be used. This function and data formatting are the job of this segment. In the 1970s, most of the networking work was about inputting and outputting info to large computers using “dumb” terminals.
Currently, there is only one choice of data format. However, the OSI protocol continues to agree on an encoding scheme. On the Internet, the only service that uses this layer is TELNET. This service provides access to servers from remote terminals. The presentation layer configures the terminal’s connection features to the server.
7) Application Layer
The application layer describes the operation of programs. For example, it specifies how they work with system files. It interacts with the presentation segment. It also represents the user interface. As a result, it transmits information and receives communication commands.
The protocols in this layer are HTTP, SMTP, POP, IMAP, and Modbus Communication Protocol.
Operating of the Network Layer in the OSI Model
The network layer connects machines in geographically different networks. In short, it provides its services to the transport segment by choosing the best path.
It is responsible for the functions of switching and routing information. It also manages logical addressing. So, it determines the procedures for exchanging data between the source and the destination. Therefore, it must know the topology of the network.
The main functions of the network layer:
- It divides the messages of the transport segment into packets. These packets contain logical addresses.
- It knows the network topology. Therefore, it manages if the source and the destination are in different networks.
- It routes the packets and determines the switching methods. Then, it transfers information through routers.
- It sends the packets using a virtual circuit or datagram. Then, it assembles the packets when they reach the destination computer.
As a result, routers work in this part. They route data packets from the source to the destination. In short, they carry data between devices using the best path.
Working of IP within the OSI Model
The IP protocol is the basic foundation of the Internet. In short, it allows data to be sent from source to destination. However, the transport level breaks the info stream into datagrams. It also breaks the datagram into fragments again during transmission.
IP Packets:
- Version 4: It allows updates.
- IHL: Header length, maximum 60 bytes.
- Service Type: It determines the reliability of data transmission.
- Total Length: Up to 65,535 bytes.
- DF (Fragmentation): The destination cannot reconnect the datagram.
- MF (More Fragments): It is not determined in the last fragment.
- Fragment Displacement: This fragment indicates which part of the datagram it belongs to.
- Time to Live: It decreases with each hop.
- Protocol: It is the transport protocol on which the datagram is based.
Understanding OSI Protocol Steps for Data Transmission
OSI implements two systematic steps when transmitting data over a network. Each step involves specific actions that do not occur in the other. In addition, each step involves its own protocol. It implements the protocols in the proper order and does the same for all computers in the network. That is, it processes the steps from top to bottom on the source computer.
OSI Protocols on the Source Computer:
- It breaks the data into smaller packets.
- It adds IP address information to the packets.
- It transmits the info over the NIC and sends it over the network cable.
OSI Protocols on the Destination Computer:
- It receives the data packets from the cable.
- It transmits them to the computer through the NIC.
- It removes the added information.
- It copies the packet info into the buffer.
- It rearranges the info and sends it to the application.
As a result, the source and destination computers must follow the same steps. Thus, the data works in the same way when sending and receiving.
Processing TCP/IP Packets in the OSI Model
Within the OSI, TCP/IP protocols allow computers to communicate over networks. In addition, these protocols are often referred to as a protocol stack. In other words, each protocol stack serves a specific purpose.
The TCP stack combines the application, presentation, and session stacks. This also means the application stack. In this process, the characteristics of the packaging for data transmission are determined. Then, the TCP application stack formats the data and sends it to the transport stack, which is the lower stack.
In addition, this stack performs the equivalent operations done by the three OSI stacks above: applications, presentations, and sessions.
The following stack is responsible for data transfer. It checks that the data sent and received are the same. In other words, it ensures that there are no errors when sending info. TCP breaks the information into pieces and adds a header to each piece. This header checks that the data is assembled when processing it correctly.
The third stack puts the data into IP datagrams. It determines the full Internet address and prepares it for delivery. The IP protocol works in the Internet stack, also known as the network stack.
That’s why it adds a header to each part. The IP header has information like the IP addresses of the sending and receiving computers. It also includes the length of the datagram and sequencing information. Because the datagram may exceed the size allowed for network packets, it breaks it into smaller packets. It then reassembles the sequencing information accordingly.
What is the Primary Reference for OSI?
A communication system requires the creation of standards between equipment from different manufacturers. These standards allow communication using the same technology. The connection between electronic equipment has become standard over time. For this reason, the OSI Model is the primary reference for network communication.
However, there are other models. However, today, most network manufacturers associate their products with the OSI model. In particular, they refer to the OSI when teaching users how to use their products. In addition, manufacturers see this standard as the best tool for learning information transmission.
The OSI reference model allows users to see network functions at each segment. This model has an understandable structure for users. It also defines and explains both IPv4 and IPv6 versions of IP.
The need to create a new version is based on the exhaustion of old IP addresses. Therefore, the OSI model was explained, and emphasis was placed on layer 3. The Internet protocol operates at this segment and determines the transmission path of info.
How Does the OSI Model Work?
The basic principle of the OSI model structure is to compare stack levels to communicate with the other party. For example, when you want to send info, your device observes the target application stack and communicates.
This communication occurs independently of network structures such as Ethernet or Token Ring. In addition, TCP combines the application, presentation, and session areas of the OSI model. In short, these areas work by gathering in the application stack layout.
Frequently Asked Questions (FAQ) About the OSI Model
- What is the OSI model, and what does it do?
- What are the layers of the OSI model?
The OSI model consists of seven levels. Each segment has specific functions:
- Physical Layer: It manages the physical connection between devices and the transmission of raw info.
- Data Link Layer: It provides reliable transmission of info over the physical link.
- Network Layer: It addresses and then manages data packets.
- Transport Layer: In addition to transmitting data reliably, it also addresses error correction issues.
- Session Layer: It establishes connections between applications or software. Thus, it has the authority to manage and terminate them when necessary.
- Presentation Layer: This provides info formatting, encoding, and interpretation.
- Application Layer: It provides network services to end-user applications.
- Why did OSI emerge?
- What layer of the OSI does the Switch operate on?
- What layer of the OSI does a Router operate on?
Conclusion
As a result, the Open Systems Interconnection (OSI) model is a fundamental concept. For this reason, it holds an essential place in the field of networking and telecommunications. Its seven-layered framework provides a common language for understanding complex systems. In addition, this structure also guides the implementation phase.
As technology evolves, the principles of the OSI model are essential. These principles provide a timeless guide for robust and compatible network solutions. In addition, this structure encourages standardization and modular design. In this way, it shapes the evolution of modern communication and networking technologies.